Identity and access management (IAM) is a framework of business processes, policies, and technologies that facilitates the management of electronic or digital identities. With an IAM framework in place, information technology (IT) managers can control user access to critical information within their organizations.
Systems used for IAM include single sign-on systems, two-factor authentication, multifactor authentication, and privileged access management. These technologies also grant the ability to securely store identity and profile data as well as data governance functions to ensure that only data that is necessary and relevant is shared.

Privileged Access Management plays a vital role while implementing Zero Trust Architecture in your organizations by enhancing the control to manage remote access.
To protect the organization’s assets and fast-track the process towards becoming compliant, Privileged Access Management should also be included to the multiple layers of security on the perimeter such as VPNs, access controls, firewalls, IDS, IPS, SIEMs, and email gateways. It focuses on the capabilities and integrations that will have the biggest impact on your business goals and security posture.

Identity and access management (IAM) is the discipline that enables the right individuals to access the right resources at the right times for the right reasons.
IAM addresses the mission-critical need to ensure appropriate access to resources across increasingly heterogeneous technology environments and to meet increasingly rigorous compliance requirements.

Role-based access control (RBAC) restricts network access based on a person’s role within an organization and has become one of the main methods for advanced access control. The roles in RBAC refer to the levels of access that employees have to the network.
Through RBAC, you can control what end-users can do at both broad and granular levels. You can designate whether the user is an administrator, a specialist user, or an end-user, and align roles and access permissions with your employees’ positions in the organization. Permissions are allocated only with enough access as needed for employees to do their jobs.


Retail

Healthcare

Insurance

Supply chain

Banking and Finance

Manufacturing


Saves time

Better security
Provides better security through careful control over access rights related to user accounts and applications by integration of authentication systems and monitoring the rights for each user.





Yes. Your account is provisioned with a single default administrator who belongs to an Administrators group within your root compartment.
Instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it. An IAM user can assume a role to temporarily take on different permissions for a specific task. A role can be assigned to a federated user who signs in by using an external identity provider instead of IAM.
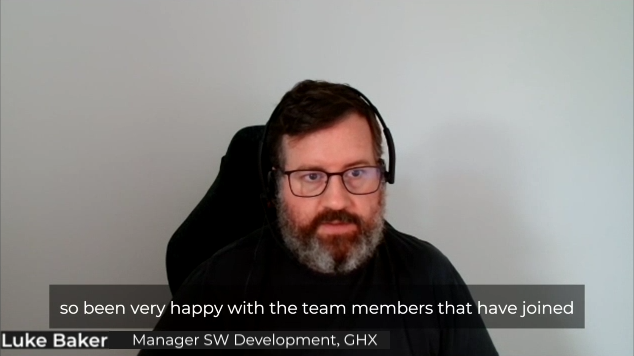
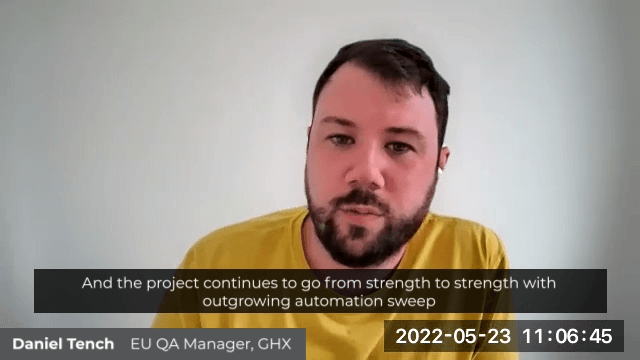
“They’re big contributors during our story grooming and design session. And they’re always very helpful and willing partners to their team members, making themselves available and really expressing a can-do attitude for getting the job done.”

Want our latest news and updates straight to your inbox ? Sign up and get it delivered.

Download Case Study